A stored Cross-Site Scripting(XSS) vulnerability was identified in Perfex CRM 3.1.6 for open ticket functionality. The vulnerability allows an authenticated(any privilege) attacker to inject malicious Javascript into the ticket submission form. The payload is stored on the server and executed when any other users, including the administrator, view the submitted ticket.
Affected Product: Perfex CRM
Affected Version: 3.1.6
Discovered By: Jobyer Ahmed
CVE: CVE-2024-8867
Vendor Response
The vendor has provided a temporary fix for the issue in the Clients.php file. The official patch will be included in the next release. The fix involves replacing the following lines:
// In application/controllers/Clients.php, replace:
'message' => $data['message'],
// With:
'message' => $this->input->post('message', false),
// This change should be made in two places within the file.
Proof of Concept
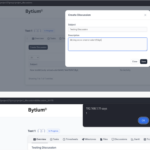
A malicious actor can inject the below payload into the message field of the ticket form:
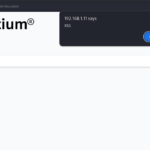
<body onload=alert("Vulnerable")>If any user or admin views the submitted ticket, it will trigger an alert demonstrating the Stored XSS vulnerability
Steps to Reproduce
Impact
Stored XSS vulnerabilities allow attackers to inject malicious scripts stored on the server and executed in the browser of any user viewing the injected content. In this case, an attacker could exploit this flaw to:
Mitigation
The developer team has been notified about the vulnerability. The developer confirmed the problem and provided a temporary solution while an official patch awaits release.
- Edit
Clients.phpand apply the vendor-provided fix. - Until an official fix, users should sanitize and validate inputs.
Note: Applied for CVE number after coordinating with possible concern team. This advisory is published to notify the users and as a part of the public reference for CVE.
Timeline
- Vulnerability Discovered: 5 Sep 2024
- Vendor Notified: 8 Sep, 2024
- Vendor Response: 9 Sep, 2024
- Additional Concern Team Response: 13 Sep 2024
- Current Status: Fixed in the later version.
Reference
Conclusion
Many custom applications require deeper analysis to discover the hidden vulnerabilities. It is always best to perform a security assessment by an expert before taking the application live.