Every business should prepare to defend its digital assets from cyber criminals. This case study proves that no one is safe from cyberattacks. In this case study, we will see how Bytium monitored the attack and responded to it.
Incident Overview
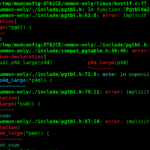
About two weeks ago, our security monitoring systems detected an unusual increase in traffic to our servers(Mr. Jobyer has posted a screenshot on his LinkedIn profile already). This activity included:
- Enumeration Attacks: Automated tools attempting to discover information about our server configurations, user accounts, and directory structures.
- RCE Attacks: Attempted to make a remote command injection.
- Cross-Site Scripting (XSS) Attacks: Attempts to inject malicious scripts into our web applications to exploit end-user browsers.
Detection and Response
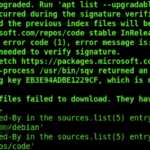
Our security operation team received numerous alerts from our monitoring systems and also blocked a lot of malicious requests automatically:
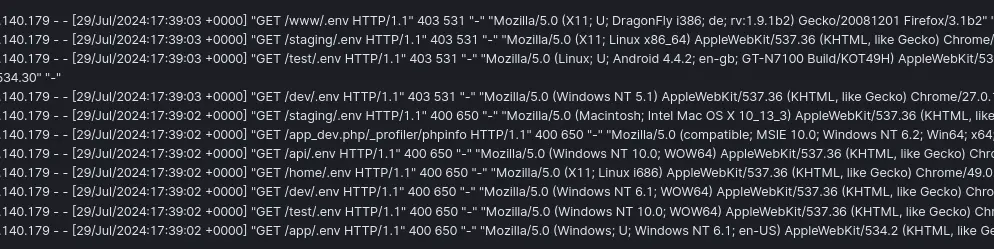
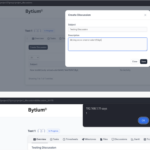
So, we quickly checked the logs manually to confirm it. We wanted to see what type of payloads the attacker sends. We were actively responding to the attacks, though(We can’t attach all screenshots for security reasons).
We believe sharing real-world attack scenarios would help others to increase awareness that no one is safe; continuous monitoring and responding is an essential task. Here are more screenshots captured today:
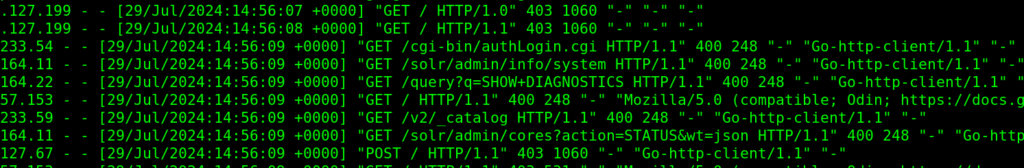
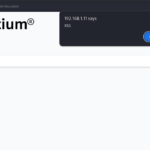
We have blocked every type of web attack successfully. And seems another try to overwhelm the server:
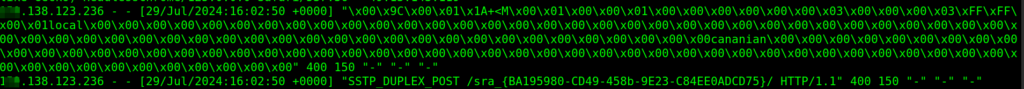
By analyzing our security system and logs, we have confirmed the following:
- Many unusual requests were sent, indicating that the attacker is continuously trying to enumerate.
- In a short time, large amount of different payloads(including RCE and SSRF) were sent.
- Tried to make a DoS attack by attempting to send different unusual patterns continuously.
Incident Response
Our intrusion prevention system(IPS) almost instantly detected and blocked attacks. The attacker thought our security monitoring was temporary, so they kept attacking. What have we done so far to mitigate these persistent attacks?
- Containment: Implemented robust firewall rules to block malicious requests, even though the firewall was in its place.
- Investigation: We investigated the logs and other alerting systems. We identified attackers who attempted to discover server-side vulnerabilities.
- Vulnerability Assessment: Reassed the security and ensured all inputs were validated correctly.
- Updated Our Custom Tool: We updated our custom-developed security tool to work more properly as another layer of security monitoring.
- Monitoring: Enhanced our monitoring systems to detect similar attacks in real-time.
Final Result
The measures we implemented successfully thwarted the attacks:
- Successfully blocking enumeration attempts.
- All input fields validated and blocked different types of attack patterns.
- Implemented multiple layers of security.
Conclusion
We are committed to protecting our client’s systems and data from cyber threats. We have seen vulnerabilities like SQL Injection or XPATH Injection, which are no longer typical for the vector. The attack pattern was more heavy and could cause more damage if successful.
Security audit and vulnerability assessment are the first steps in protecting systems and data from cyber threats, and continuous security monitoring is an essential part of early detection and faster response.
If you want the same level of protection from cyber threats to protect your systems and applications, don’t hesitate to contact us. We are located in the USA and also Bangladesh.