Protect Your Business
Cybersecurity Services For Businesses in Bangladesh
As a global IT company specializing in cybersecurity, provide top-notch services worldwide. With a dedicated, highly experienced cybersecurity team in Bangladesh, we have tailored our cyber security services to protect Bangladeshi businesses from modern cyber threats. Work with Bytium and feel the true difference with other providers today!
True Security Assessment
Security assessment is not simple as scanning with automated tools. It requires true hacking skills and experience for true security assessment. Experience it today and see the difference with others!
SIEM and SOC Solutions
Managed SIEM and SOC saves time and money. Let us monitor your security incidents and respond in a timely manner or build your own infrastructure . We are trained, and professional!
Systems Hardening
We excel at finding and fixing vulnerabilities in your digital infrasctructure and Applications. Our security expertise allows you to rely on us to identify weaknesses and mitigate them effectively.
Is your business located in Bangladesh?
Insufficient security assessments by unskilled experts leave many businesses in Bangladesh vulnerable to cyber attacks. Safeguard your business starting today with our comprehensive protection services by certified experts.







Extertnal security assessment is the first line of defense
External Perspective
Discover Real Vulnerabilities
Tailored Security Assessment Services
We rely on effective, legitimate scanners for cybersecurity. Our professional team in Bangladesh uses manual testing and award-winning tools to keep your infrastructure, digital devices, and web applications safe from cyber threats.
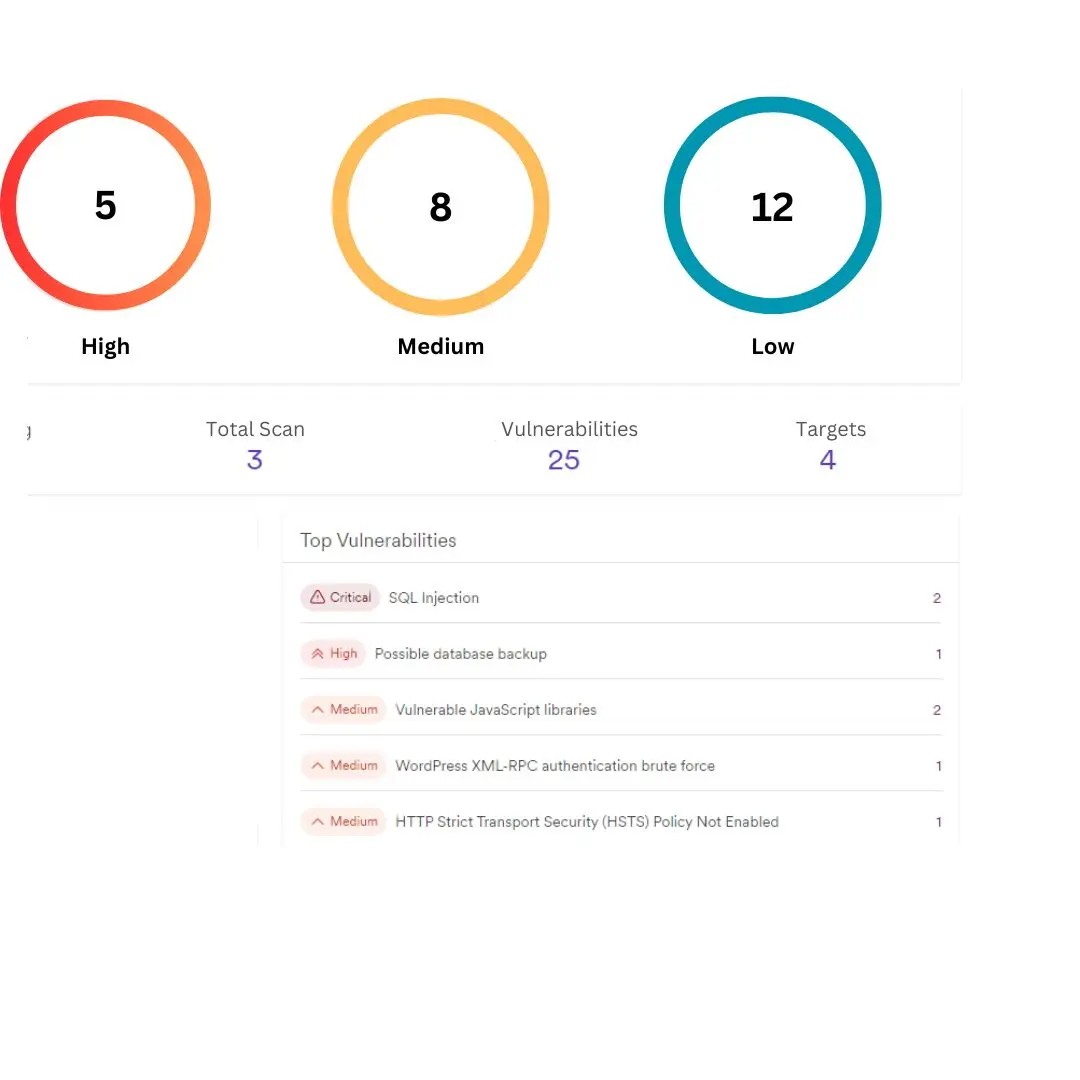
Vulnerability Assessment
In Bangladesh, vulnerability assessment is also known as vulnerability scanning. At Bytium, it is 70% automated and uses 30% manual vulnerability scanning. We don’t provide you with a report generated by an easy-to-use scanner.
Penetration Testing
We understand very well, vulnerability scanning is not penetration testing. Our penetration testing service is real-world simulated attack that requires 30% automatic and 70% manual scanning and exploit attempts.
Red Teaming
The Bytium team emulates the true hacker group. It uses a goal-based method to test your employees, applications, and Active Directory.
Limited-time offer: Special discounted pricing is available for businesses located in Bangladesh.

Security Monitoring Solutions
Affordable solutions for continuous security monitoring. Arm your team with our tailored security monitoring solutions.
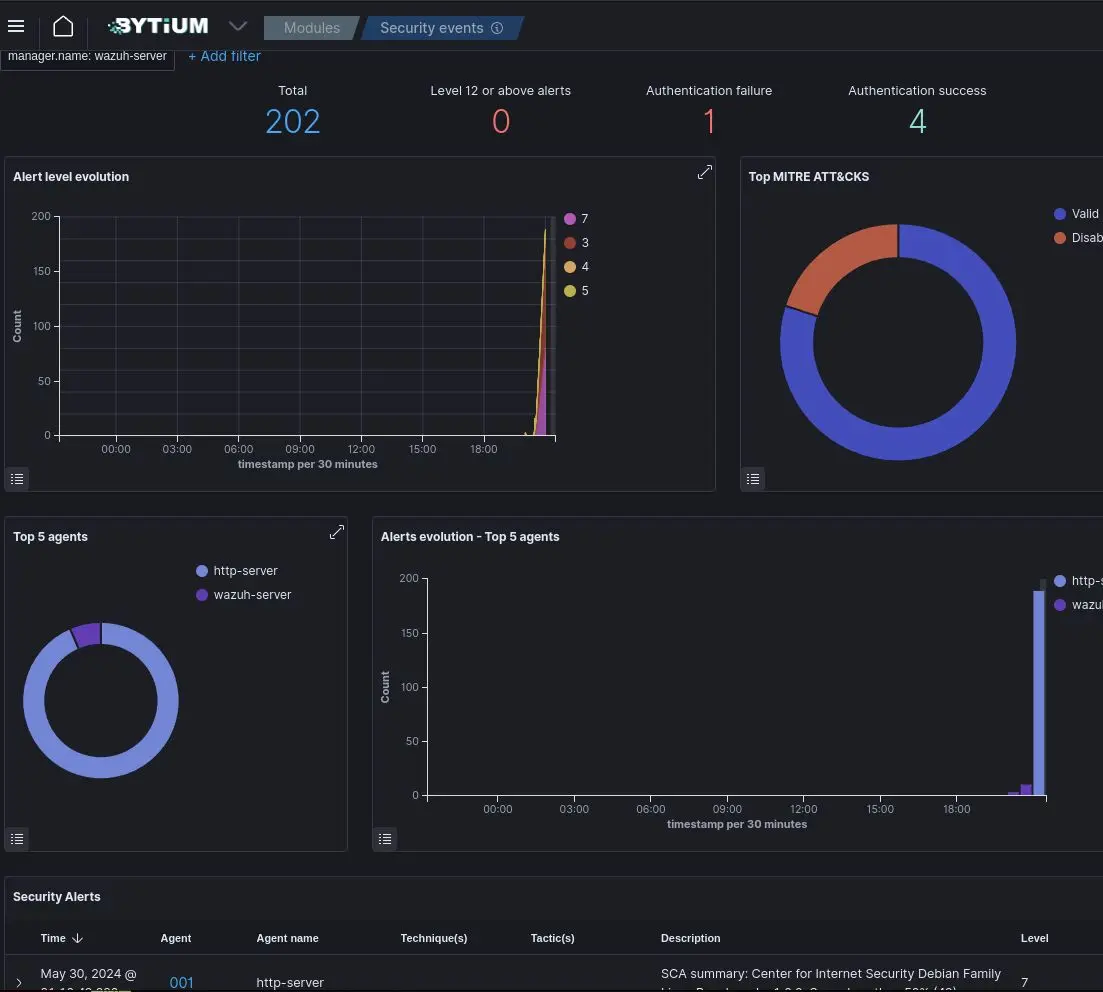
Managed SIEM and SOC Solutions
Tools and Experts are ready to use. We are your MSSP. We monitor, alert, and suggest solutions to every incident.
Systems Hardening
We can audit your systems and application’s code and apply possible patches to harden your systems.
In-house SOC implementation
We can help your business to implement its own security operation center with open-source tools.
Key Benefits
Why we’re the best choice for your cybersecurity needs
We are a globally recognized IT company with a strong presence in the USA and Bangladesh. Our skills, experience, and working style set us apart from others. We are the only company in Bangladesh that offers highly skilled cybersecurity experts to protect your digital assets.
Less expensive but high-quality
We have designed these services to be extremely cost-effective for businesses of all sizes in Bangladesh. We never compromise on quality and take great pride in our reputation.
True Cybersecurity Service in Bangladesh
We truly understand how cyber attack works. This means that we have the best method to protect your assets from attacks. It is not a one-click security scanning service.
Certified and experienced
Our team is led by Jobyer Ahmed and is led by certified experts with extensive experience. An exclusive OSCE3 holder (OSEP, OSED, and OSWE) in Bangladesh, as well as OSCP, Pentest+, and Security+ certified.
Customized solutions
We recognize that every organization has distinct needs and financial considerations. That’s why our cybersecurity services for businesses in Bangladesh are incredibly customizable.
FAQ
If you have different questions, feel free to contact us.
It is a process of identifying, classifying, and analyzing computer systems, applications, and other digital device’s security weaknesses with automated tools. Our vulnerability scanning combined with manual checking to avoid any false positives. Vulnerability scanning is considered the minimum and first step to protect your digital assets from cyber threats.
Penetration testing is a simulated security assessment method performed by certified and skilled experts to identify weaknesses that attackers can exploit. Vulnerability scanning utilizes automated tools, while penetration testing mostly involves manual testing and often attempts to exploit vulnerabilities to understand their real impact. Unfortunately, in Bangladesh, most Managed Security Service Providers (MSSPs) label vulnerability scanning as “VAPT” (Vulnerability Assessment and Penetration Testing), even though it is actually just vulnerability scanning. The Bytium team usually plans the test, analyzes vulnerabilities, attempts to exploit them, and if necessary, creates new tools or uses commercial ones.
Red teaming is simulating or emulating a real-world attacker’s method(Known as TTPs) to assess an organization’s security. The security professional team will act as a real attacker and attempt to access the organization’s internal network in different ways. The goal of red teaming is to test the defense, response capability, and overall security of the organization.
Penetration testing, often confused with red teaming, involves simulated cyber attacks performed by security professionals to exploit vulnerabilities. In contrast, red teaming is an adversarial exercise in which experts mimic real-world attacks to evaluate an organization’s overall security posture, including its capability to detect and respond to advanced threats. Red teaming often includes bypassing various security defenses, exploiting human or physical vulnerabilities, and creating custom tools.
There are several reasons, why we should be your first choice for cybersecurity services:
- Highly affordable.
- Highly skilled and Experienced.
- Our experts are OSCE3, OSEP, OSED, OSWE, OSCP, Pentest+, Security+ certified.
- Balanced between manual and automated assessment.
- Instant support.
- Bytium is a globally known IT company. Legally operated in the USA and Bangladesh.
No. We don’t have any free security assessment service.
In Bangladesh, security assessment is often referred to as VAPT(Vulnerability Assessment and Penetration Testing). But, in reality, VA or vulnerability assessment is a different service. Penetration testing is a simulated testing method and is always included with any type of penetration testing by default. If you say “Penetration testing”, you don’t need to mention “VA”, because it is part of the penetration testing service.