Domain Name System is also known as the phonebook of the Internet. DNS translates domain names to IP addresses. Suppose someone browses bbc.co.uk; the DNS will be responsible for finding the correct website address to load.
However, as DNS plays a critical role, it became a prime target for cyber attacks. It is essential to understand these threats to safeguard your infrastructure. Let’s quickly look at the trended and top 10 DNS security threats!
DNS Spoofing Attack
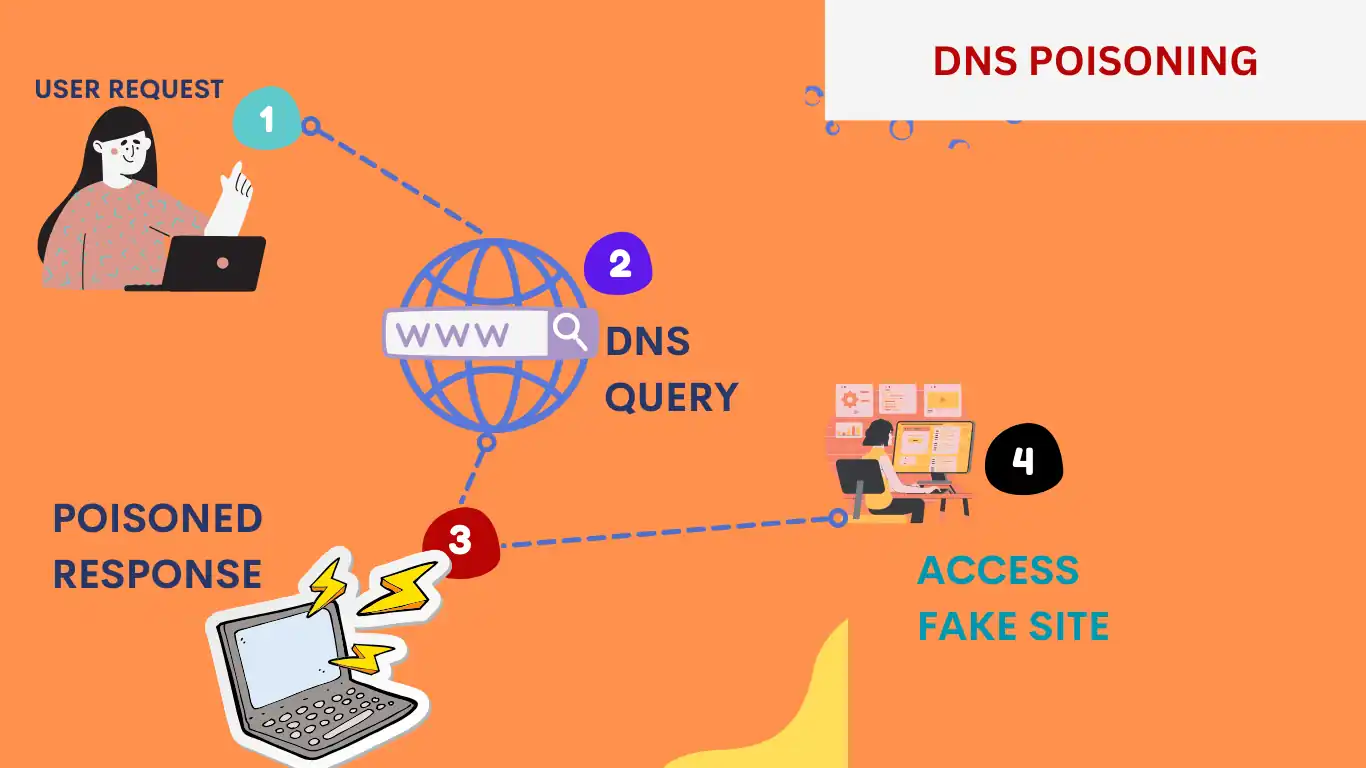
DNS Spoofing, and some people call it DNS Cache Poisoning. Malicious actors inject false records by DNS spoofing attacks into the DNS resolver’s cache, which can be used to launch different types of attacks, such as redirecting users to malicious websites that steal users’ confidential data or distribute malware. DNS Spoofing attacks can be prevented with NDSSEC(DNS Security Extension), Regular Updating and patching vulnerabilities, and validating the response.
DNS Amplification Attack
Domain Name System Amplification is a kind of DDoS or Distributed Denial of Service attack. DNS Amplification attacks usually exploit the functionality of the DNS Server to envelop a target with traffic flooding.
The malicious actor sends a DNS query to the public server with the victim’s spoofed IP address for a successful amplification attack. The query is designed to derive a large response from the server. As the IP address is spoofed, the response is sent to the victim’s IP address. This attack can be prevented by configuring rate limit and ingress filtering.
DNS Tunneling Attack
DNS tunneling means sneaking data or directions through a network firewall or proxy using DNS queries and responses. DNS Tunneling attacks are often used for malicious purposes such as bypassing security, data exfiltration, or for command and control activities.
The attacker uses a server to receive malicious DNS queries, which are then decoded and processed by the server. The attacker’s client encodes the data within DNS queries and sends them to the compromised DNS server. The receiving server decodes the data, processes it, and can also send back encoded responses.
NXDOMAIN Attack
NXDOMAIN attack is a DNS flood attack. With this cyber attack method, the attacker floods the server with non-existing requests as the NXDOMAIN, which means the domain name does not exist.
Let’s see it in action with the below’s script:
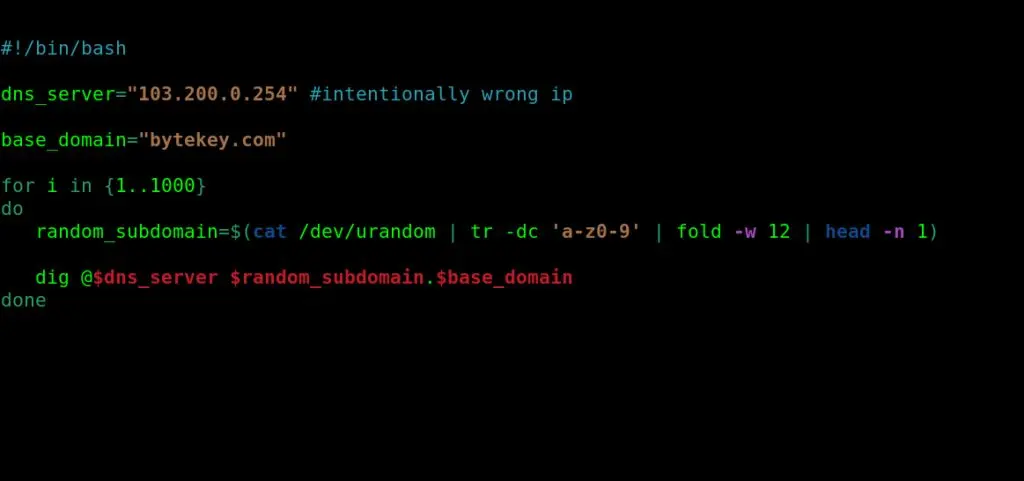
If we run the script, we will get the following response:
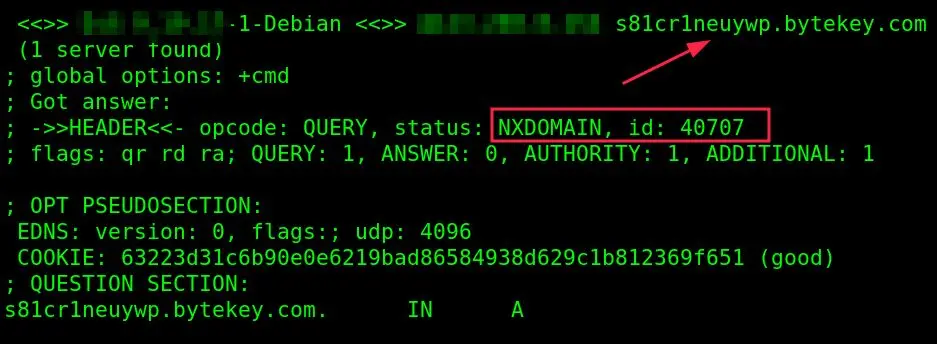
NXDOMAIN attacks can be prevented by configuring And limiting the DNS server, DNS caching, and distributing the load across multiple servers.
Subdomain Takeover Attack
Some businesses configure subdomain points to third-party services like cloud or web host services for temporary use. And many of them forget to clean the DNS record once the use of the service no longer exists. This mistake creates a vulnerability for attackers to take over the subdomain. Let’s see an example.
Imagine the attacker used the following command:
dig +noall +answer CNAME legit.bytium.comAnd found legit.bytium.com points to the GitHub page legit-byte.github.io , which no longer exists. The attacker would create a new repository with the same name and host web pages for phishing and other malicious purposes.
Regular security audits, proper external service configurations, and access control management can prevent Subdomain Takeover attacks.
Pharming Attack
This is a DNS Attack method to redirect users to fake websites. The pharming attack can be executed by modifying the user’s host file or with a DNS poisoning attack. A pharming attack is a more stealthy cyber attack, making it more dangerous.
DNS Hijacking Attack
DNS hijacking is a cyber attack method that redirects DNS queries to a different DNS server. As a result, users can redirected to malicious websites and intercept communications. DNS Hijacking methods include:
- Local DNS Hijack: Viruses can modify the user’s computer DNS Configuration to redirect to a malicious server.
- Router DNS Hijacking: The attacker may gain access to the router and alter the DNS record.
- Man-in-the-Middle attack: The attacker launches an MTM attack, intercepts communications, and alters the response.
It is important to use DNSSEC and HTTPS; using trusted DNS servers and scanning regularly for malware can help defend against DNS Hijacking attacks.
Fast Flux DNS Attack
Fast Flush DNS attack is a method to change the IP address of a domain rapidly. Attackers choose Fast Flux DNS attacks to hide their phishing and malware delivery sites behind multiple IP addresses. Let’s see how it works –
- IP Address switching: The attacker can change the DNS records constantly. This can be done automatically by altering A records.
- Use of Botnets: A large amount of IP addresses can be from the attacker’s botnet.
- Double Flux: It involves changing the A record, as well as the NS record.
DNS Rebinding Attack
DNS Rebinding is a cyber attack that manipulates how web browsers interpret domain names to bypass security boundaries. Malicious JavaScript is used to change the DNS entry for their domain to point to a target IP address within the user’s local network, allowing them to interact with devices on the network. This process circumvents the browser’s same-origin policy, restricting web pages from accessing resources from different domains.
Zero-Day DNS Attacks
Zero-Day DNS attacks involve exploiting previously unknown vulnerabilities in the domain name system. In this kind of attack, the vulnerabilities exploited by attackers are entirely unspecified to the developer. The impact can be widespread, affecting information dissemination, data security, and service continuity. For instance, attackers might exploit a flaw in DNS server software to redirect legitimate website traffic to fraudulent sites, leading to potential phishing or malware distribution. Regular software updates, advanced intrusion detection, and proper incident response are crucial to defend from Zero-Day DNS attacks.
Conclusion
For an organization, It is crucial to understand the type of DNS threat to defend against it. DNS Spoofing, Amplification, or Fast Flux DNS attacks pose different and unique challenges. Regular security audits, applying best practices, and staying informed about the latest cybersecurity trends are crucial to safeguarding infrastructures from such vulnerabilities.
If you or your organization require technical assistance or to strengthen the defense, feel free to contact us. Bytium is a trusted name that offers comprehensive vulnerability assessment and, penetration testing and custom security audit services worldwide.